Proving Grounds | Nickel
Scanning:
Nmap scan report for 192.168.245.99
Host is up, received user-set (0.24s latency).
Scanned at 2021–08–16 23:32:11 EDT for 434s
Not shown: 65528 filtered ports
Reason: 65528 no-responses
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack FileZilla ftpd
| ftp-syst:
|_ SYST: UNIX emulated by FileZilla
22/tcp open ssh syn-ack OpenSSH for_Windows_8.1 (protocol 2.0)
| ssh-hostkey:
| 3072 86:84:fd:d5:43:27:05:cf:a7:f2:e9:e2:75:70:d5:f3 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDYR4Bx82VWETlsjIFs21j6lZ6/S40jMJvuXF+ay4Qz4b+ws2YobB5h0+IrHdr3epMNFmSY8JXFWzIILhkvF/rmadXRtGwib1VZkSa3nr5oYdMajoWK0jOVSoFJmDTJvhj+T3XE7+Q0tEkQ2EeGPrz7nK5XWzBp8SZdywCE/iz1HLvUIlsOqpDWHSjrnjkUaaleTgoVTEi63Dx4inY2KS5mX2mnS/mLzMlLZ0qj8vL9gz6ZJgf7LMNhXb/pWOtxfn6zmSoVHXEXgubXwLtrn4wOIvbZkm5/uEx+eFzx1AOEQ2LjaKItEqLlP3E5sdutVP6yymDTGBtlXgfvtfGS2lgZiitorAXjjND6Sqcppp5lQJk2XSBJC58U0SzjXdyflJwsus5mnKnX79nKxXPNPwM6Z3Ki1O9vE+KsJ1dZJuaTINVgLqrgwJ7BCkI2HyojfqzjHs4FlYVHnukjqunG90OMyAASSR0oEnUTPqFmrtL/loEc3h44GT+8m9JS1LgdExU=
| 256 9c:93:cf:48:a9:4e:70:f4:60:de:e1:a9:c2:c0:b6:ff (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBDJYE805huwKUl0fJM8+N9Mk7GUQeEEc5iA/yYqgxE7Bwgz4h5xufRONkR6bWxcxu8/AHslwkkDkjRKNdr4uFzY=
| 256 00:4e:d7:3b:0f:9f:e3:74:4d:04:99:0b:b1:8b:de:a5 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIL8cLYuHBTVFfYPb/YzUIyT39bUzA/sPDFEC/xChZyZ4
135/tcp open msrpc syn-ack Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack Microsoft Windows netbios-ssn
3389/tcp open ms-wbt-server syn-ack Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: NICKEL
| NetBIOS_Domain_Name: NICKEL
| NetBIOS_Computer_Name: NICKEL
| DNS_Domain_Name: nickel
| DNS_Computer_Name: nickel
| Product_Version: 10.0.18362
|_ System_Time: 2021–08–17T03:38:14+00:00
| ssl-cert: Subject: commonName=nickel
| Issuer: commonName=nickel
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2021–08–16T03:29:57
| Not valid after: 2022–02–15T03:29:57
| MD5: 7e08 0ce0 b27b 9542 3c79 42c6 d4f6 c522
| SHA-1: 89c1 2437 318a 88d8 2da2 7c90 b74c 90a9 aff6 efdc
| — — -BEGIN CERTIFICATE — — -
| MIIC0DCCAbigAwIBAgIQXxTaaHntc6RG6qwReBQG+DANBgkqhkiG9w0BAQsFADAR
| MQ8wDQYDVQQDEwZuaWNrZWwwHhcNMjEwODE2MDMyOTU3WhcNMjIwMjE1MDMyOTU3
| WjARMQ8wDQYDVQQDEwZuaWNrZWwwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEK
| AoIBAQDly/vmp00kCX31dd9QTeRGu3ItdtQNYM4TJrK99vAuh5uDYWlr5f6VRUZb
| toKy2GCJLwTATLU7GOiOu/Q1asag3CitGi01gq23WEkOgrBW2+AyKi38R1+hYsFn
| 1wHH5HlUbTQN33yhDVXwPdxnqXh1oAiCBvOOZfBSiAgWTUBooA7YM9tJVmtkT+bi
| DYaG3ZF4RS3shMquqEg9490Tto4RN3USeuzLEDZXLAiQeapL3ZbPcNGZHEWPduZN
| 6yfEryzOh535Kg6Nkte/aapnwit/HFJN/drCKxciizU+/ahUOXVvmuSppInMVftT
| bj01sS5csyHdOKetsc16+OsRg+6dAgMBAAGjJDAiMBMGA1UdJQQMMAoGCCsGAQUF
| BwMBMAsGA1UdDwQEAwIEMDANBgkqhkiG9w0BAQsFAAOCAQEAQldeETsyCBBGQXdx
| yADpn59iFzJOdu5X6VA1iHcU74J/7qe8VCitUrX0jSmWhyz4Vqy1oTH/0K70QSZR
| 7Jftjr+FWXOpTTCo6TDKWN1vdg96w8vA0/dnCttsrmwpLuiyu/0aBt/wBYzOQD4p
| 2e2/CrCkuGJIjiMVbmxMp9hM1gpS+lMBiGD8AgbTIAbq/oTvEkL2BiAuizEYfyRT
| F9zSdLM2fRlzaI4y/0Hb7z+mWK/VMtAPNzppYXxyZbaumwgamnBE683evE11k+q+
| oeFr45YjptfhgSOX9cEOl7KFhoJkh02XM2ijNUtrnsxGEXSf0IFqy4/xCmkW41zG
| FgpiZw==
|_ — — -END CERTIFICATE — — -
|_ssl-date: 2021–08–17T03:39:25+00:00; +1s from scanner time.
8089/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-favicon: Unknown favicon MD5: 9D1EAD73E678FA2F51A70A933B0BF017
| http-methods:
|_ Supported Methods: GET
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Site doesn’t have a title.
33333/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-favicon: Unknown favicon MD5: 76C5844B4ABE20F72AA23CBE15B2494E
| http-methods:
|_ Supported Methods: GET POST
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Site doesn’t have a title.
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Upon visiting the web service on port 8089, we can see that there seems to DevOps APIs on the server.

Once we click any of them, we are redirected to a different address and port. I’m suspecting the ip address we are being redirected to must be a different IP address for the same machine.

Intercepting it on Burp, then changing the request to POST, I get a different ERROR. On this one, it’s saying that I should have a Content-Length header.
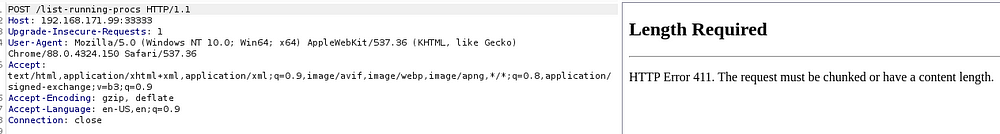
After adding the Content-Lenth header, we finally get a proper communication with the API. More importantly, we can see running processes on the machine, plus some delicious creds → ariah:Tm93aXNlU2xvb3BUaGVvcnkxMzkK


After decoding the base64 password, we can ssh into the machine using the creds → ariah:NowiseSloopTheory139

We are also able to login FTP using ariah:NowiseSloopTheory139
Inside ftp, we find a password-protected pdf. And using, hashcat, we were able to the password.



Privilege Escalation:
- We are able to access the internal site via port 80.. note that port 80 was not listed in our nmap scan.

2. As detailed on the pdf we got our hands on, http://nickel/? is a command endpoint, let’s try it out if we can execute commands on it.

We can, and it seems the commands are ran with system privs. Figuring out how to get a reverse shell or persistent access to system account was took me hours to figure out, honestly.
Takeaway:
1. didn’t use cmd /c effectively
2. URL-encode the whole command after ?
3. Firewall rules. tried port 21 port 22 port 53 for reverse shell, but didn’t work.. What worked was port 443 and port 80
I had thought a varierty of these ideas, but missing one or the other everytime I tried any of them.. e.g. url-encoded the command but missing cmd /c or used cmd /c, url-encode but ports were firewalled..
What also worked for me → transfer nc.exe to the target host and start a listener there, then connect to the internal listening port to avoid the fuss with firewall rules.

